GUIDE
3 Minute Credential Capture using The Social-Engineer Toolkit (SET)
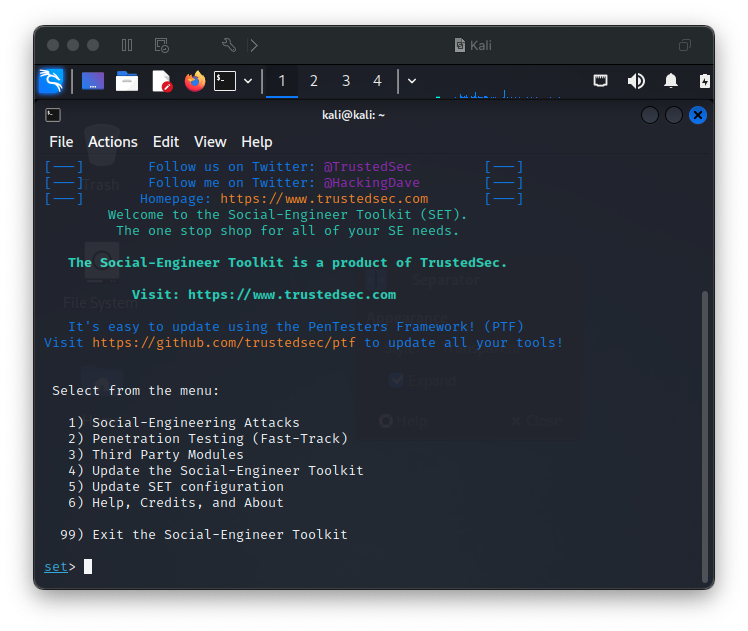
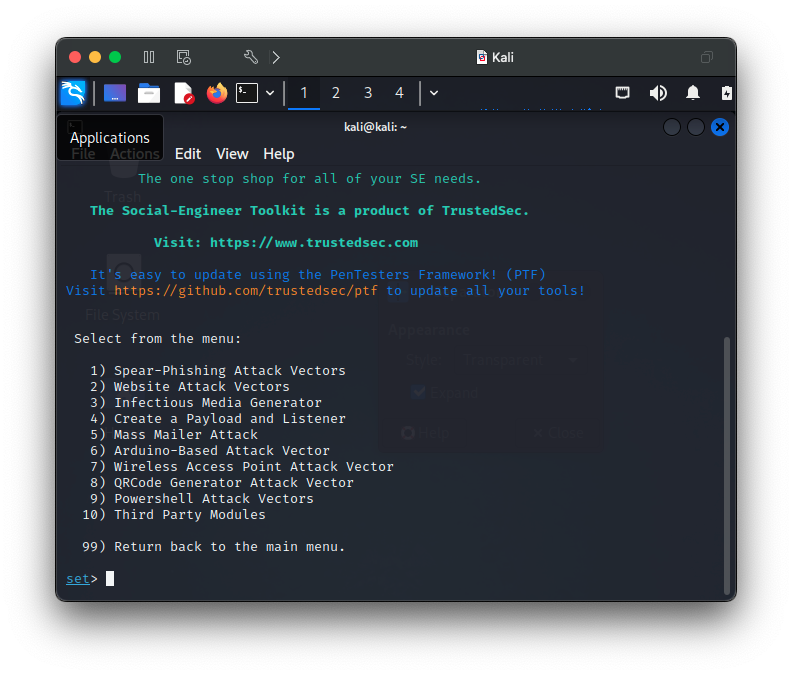
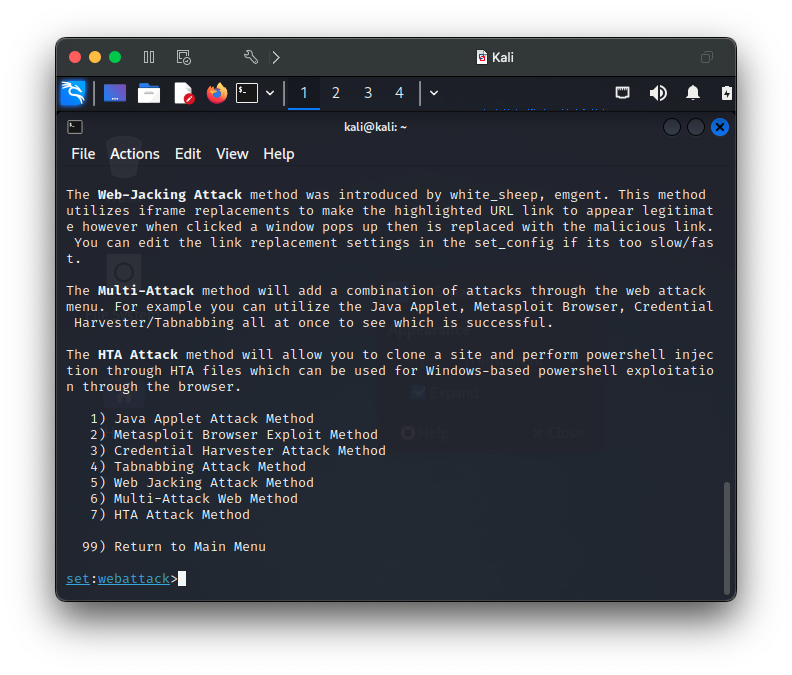
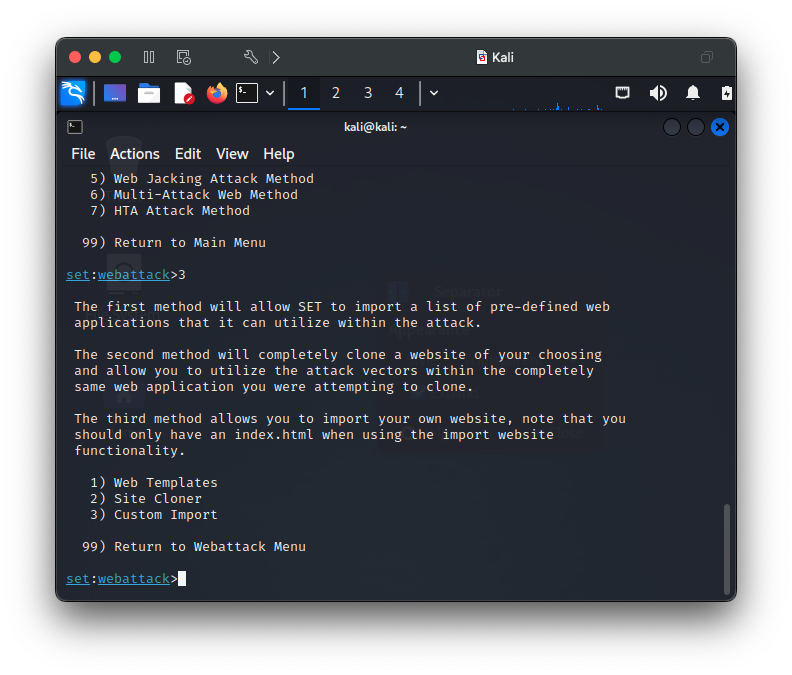
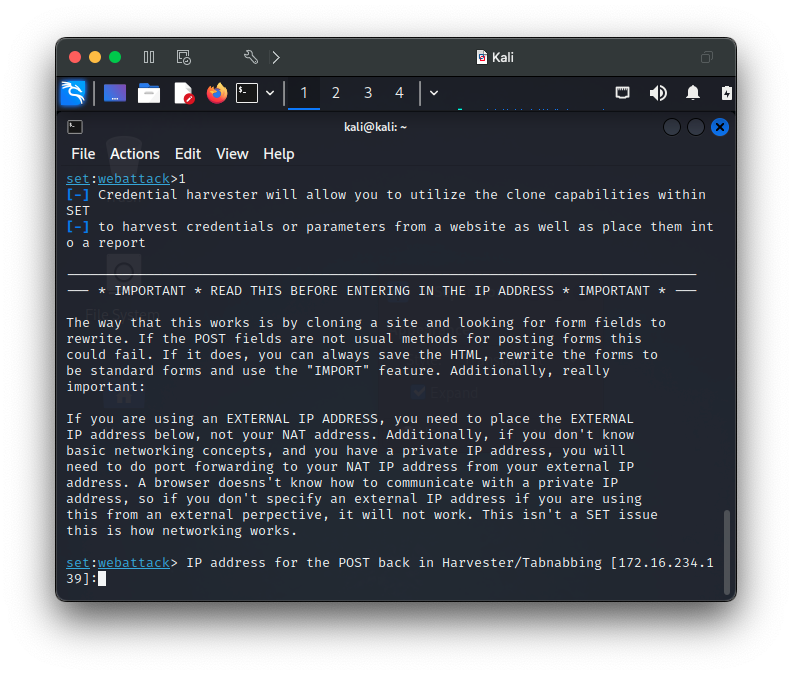
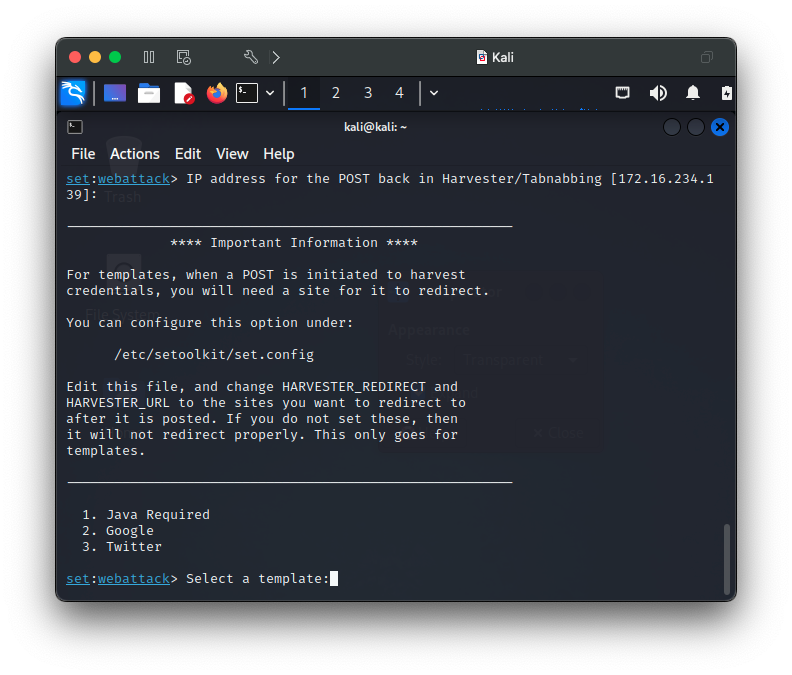
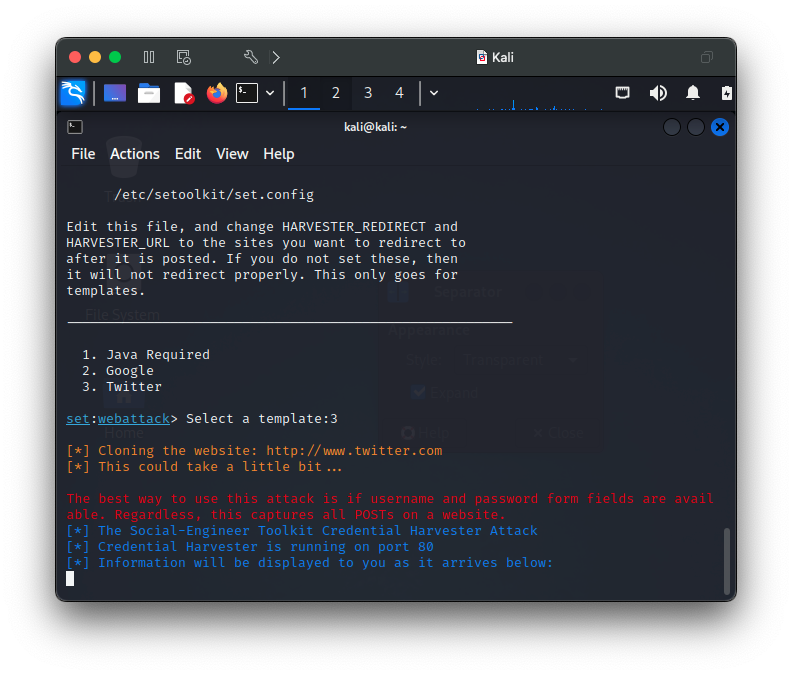
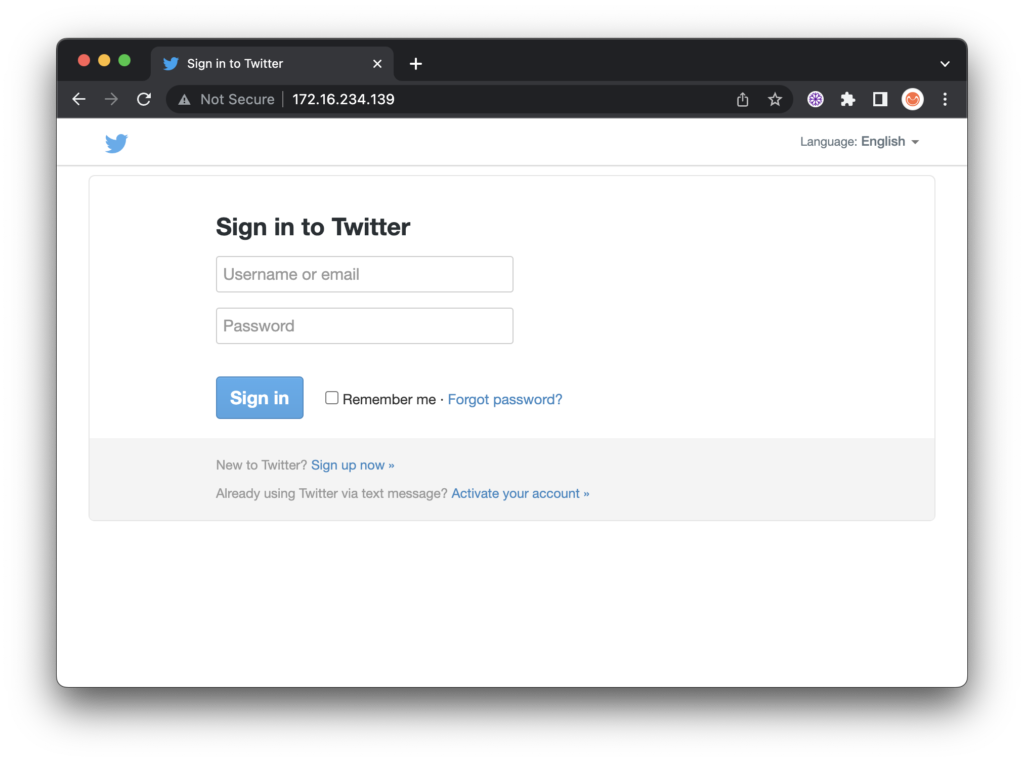
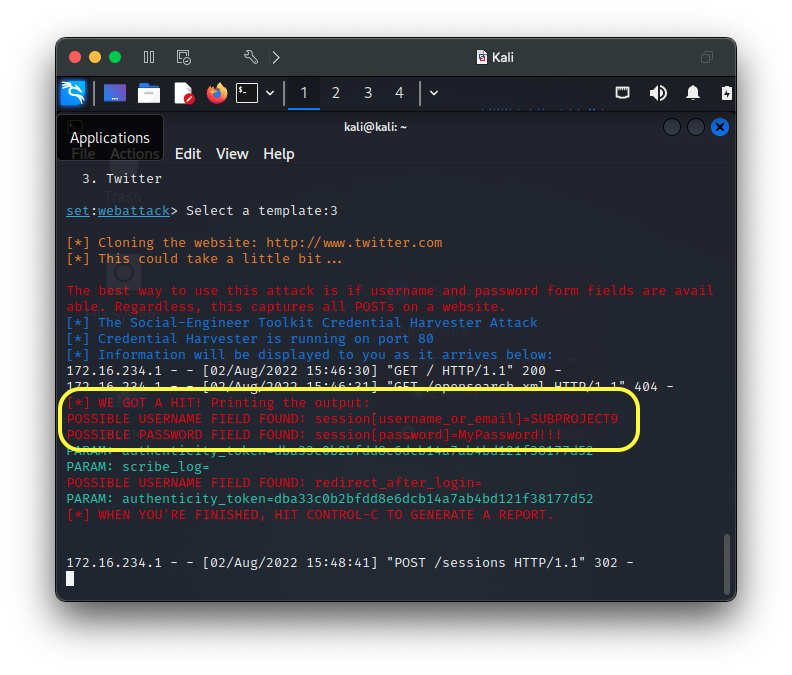
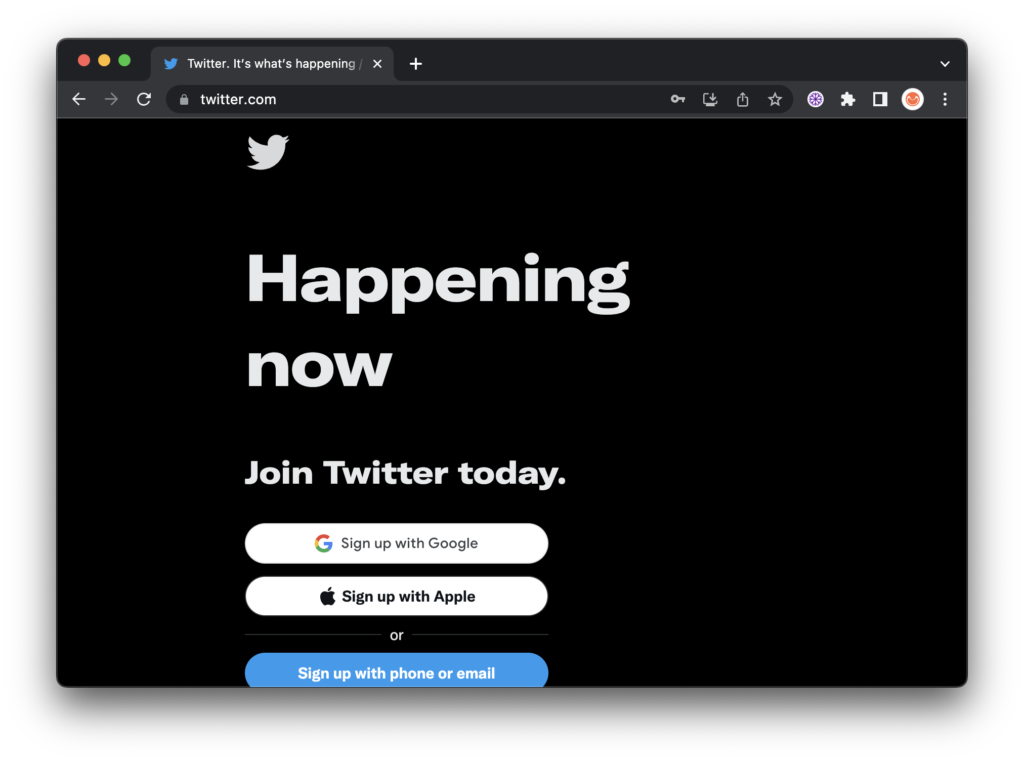
This is a very simple, yet powerful attack that spoofs a legitimate webpage to capture credentials in minutes with the Social-Engineer Toolkit (SET). I use adaptations of this procedure to simulate phishing type attacks for presentations to illustrate how easy and simple dangerous attacks can be. SET is a very powerful tool with many powerful options and features that SET makes easy to deploy.